This is a comprehensive Ethical Hacking (security penetration testing) hands-on training! You will participate in live discussions, demos, whiteboard instruction and lab exercises. No prior experience is needed.
The author (Omar Santos) will walk you through numerous exercises and ethical hacking concepts.
If you are starting your cyber career, seeking your Certified Ethical Hacking (CEH), CompTIA PenTest+, or Offensive Security Certified Professional (OSCP) Certification, or just interested in learning more about cyber security, this three-day training session is a great resource!
This course provides step-by-step real-life scenarios.
It starts by going over passive and active recon, then dives deep into scanning, target exploitation, password attacks, web application testing, buffer overflows, wired and wireless network hacking, and post-exploitation techniques.
You will use dozens of penetration testing tools and learn how to build your own lab!
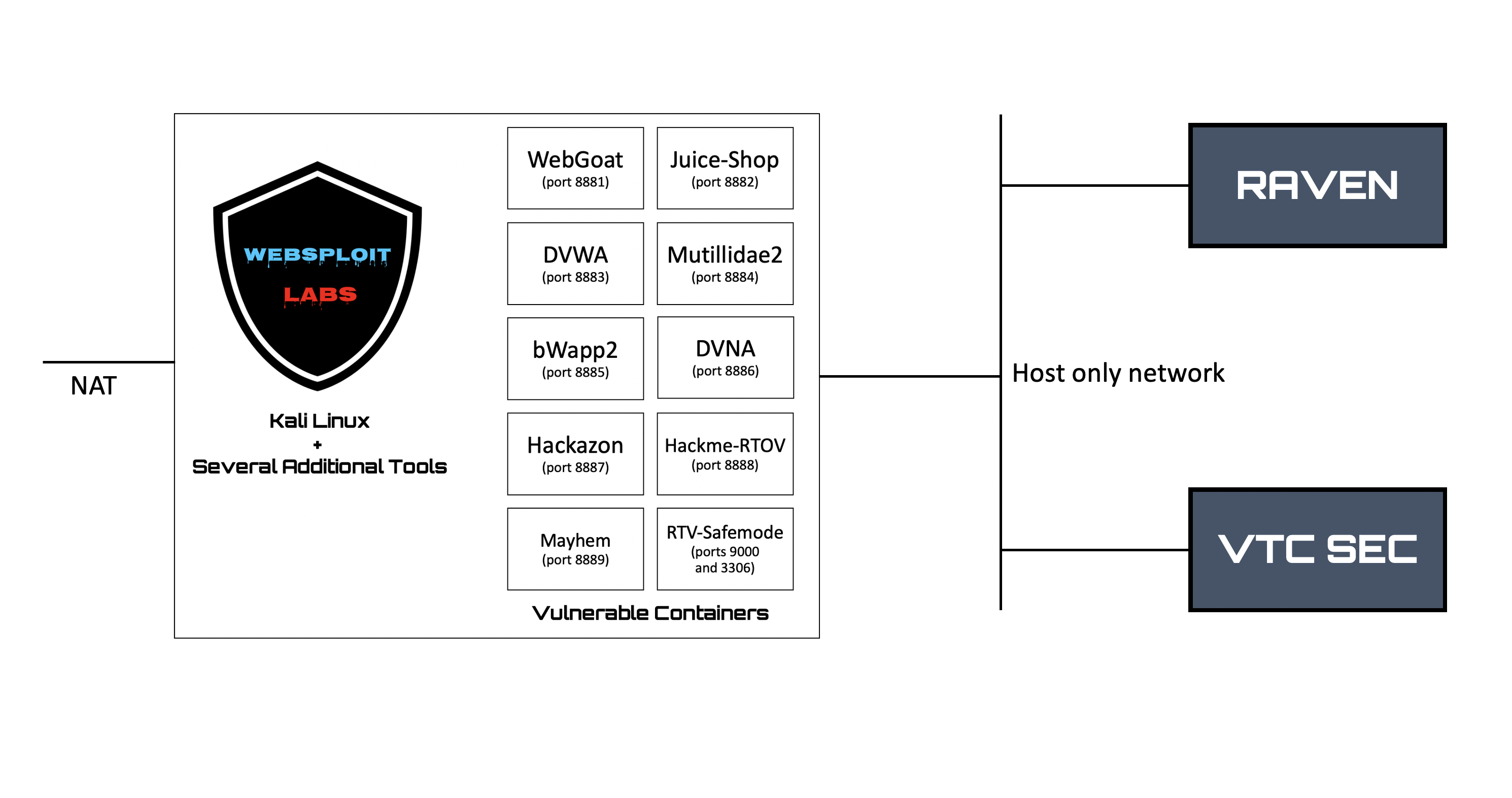
Kali + Additional Tools + Vulnerable Applications in Docker containers...
A vulnerable VM that you will use to perform a full assessment (from reconnassaince to full compromise)
Another vulnerable VM that you will use to perform a full assessment (from reconnassaince to full compromise)
This video explains how to setup the virtual machines in your system using Virtual Box.
The diagram below shows the lab architecture with WebSploit Full version, Raven, and VTCSEC. The VMs were created in Virtual Box. It is highly recommended that you use Virtual Box. However, if you are familiar with different virtualization platforms, you should be able to run the VMs in VMWare Workstation Pro (Windows), VMWare Fusion (Mac), or vSphere Hypervisor (free ESXi server).
You should create a VM-only network to deploy your vulnerable VMs and perform several of the attacks using WebSploit (Kali Linux), as shown in the video above. You can configure a separate network interface in your WebSploit VM to connect to the rest of your network and subsequently the Internet. Preferably, that interface should be in NAT mode.

Stay in Touch with Omar!